Recently, a significant vulnerability has come to light, putting millions of servers operating on the Google Cloud Platform (GCP) at risk. Dubbed CloudImposer, this security flaw potentially allows attackers to launch remote code execution (RCE) attacks, creating an alarming situation for users and businesses relying on this cloud infrastructure.
Table of contents
ToggleWhat is the CloudImposer Vulnerability?
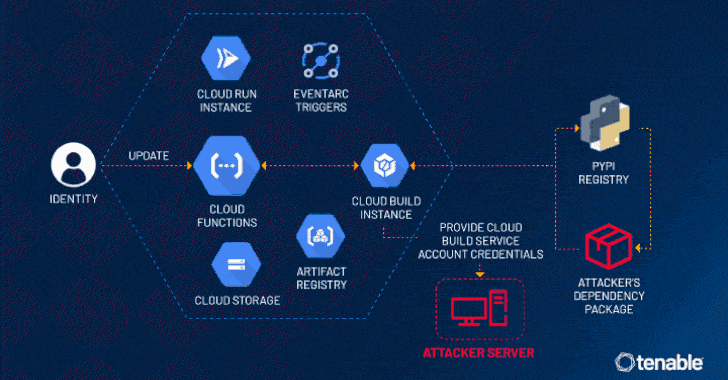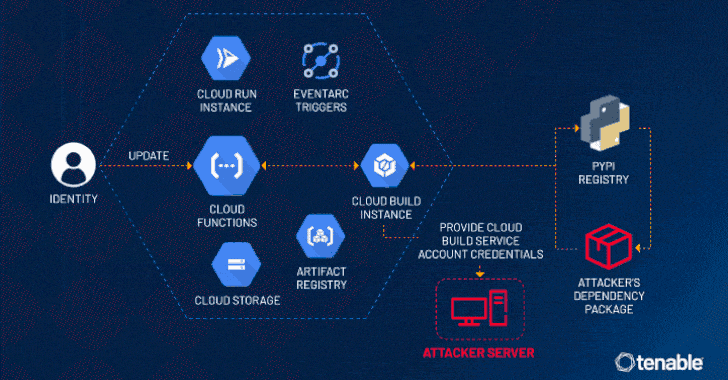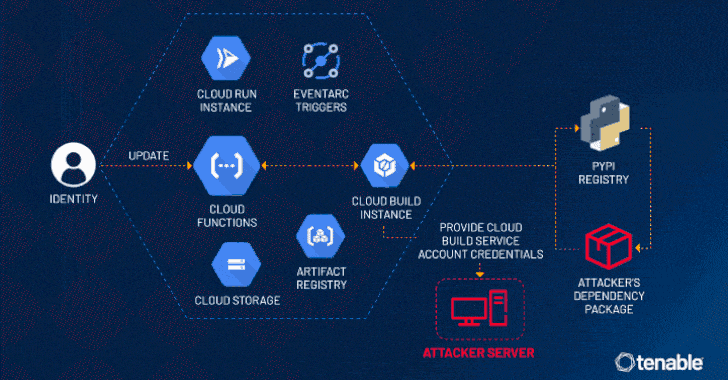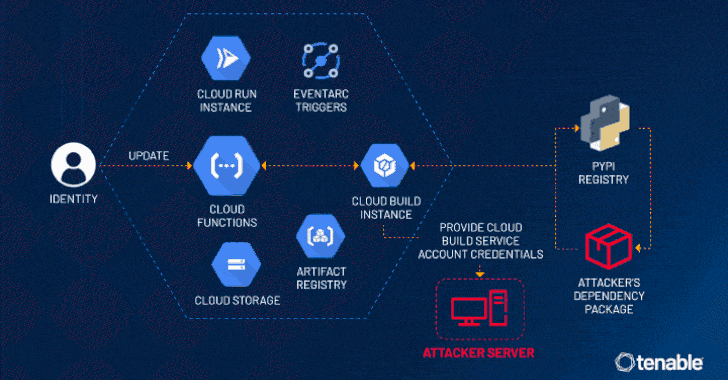
The CloudImposer vulnerability is a dependency confusion flaw that could enable attackers to exploit various services within Google Cloud. This vulnerability opens the door for malicious actors to execute arbitrary code on affected servers, which could lead to data breaches and unauthorized access to sensitive information.
Impact on Google Cloud Platform
According to recent research findings, millions of servers that operate on the GCP may be susceptible to attack due to this critical flaw. The reach of the CloudImposer vulnerability raises significant concerns amongst users and developers who depend on the security and stability of Google Cloud for their operations.
Privilege Escalation Concerns
Researchers have also discovered another related flaw known as ConfusedFunction, which presents a privilege escalation vulnerability within Google Cloud Platform’s Cloud Functions service. This vulnerability allows attackers to gain higher levels of access within the cloud environment, potentially compromising the security of connected applications and user data.
Tenable’s Discovery and Resolution
The critical flaws, including the CloudImposer vulnerability, were uncovered by Tenable Research, which has made significant strides in raising awareness about these serious security issues. In response to the findings, Google has quickly addressed the vulnerabilities found in their Composer software tool, implementing patches to fortify the defenses against potential threats.
The Broadening Threat Landscape
As cyber threats continue to rise, Google Cloud’s latest security report indicates an increasing trend in vulnerabilities discovered within the platform. This highlights the ongoing risks that cloud technologies face and the necessity for robust security measures to safeguard user data against emerging threat vectors.
Need for Vigilance
The revelation of vulnerabilities like CloudImposer and ConfusedFunction emphasizes the critical need for organizations utilizing Google Cloud to proactively manage their security posture. Regular updates, continuous monitoring, and rigorous testing are essential to mitigate the risks posed by these vulnerabilities and to ensure a secure operating environment.

"Vulnerability is our most accurate measurement of courage." @BreneBrown
— TED Talks (@TEDTalks) July 19, 2018
Watch Brené's full TED Talk about the power of vulnerability here: https://t.co/4Hp4rSlOej pic.twitter.com/ykeanJbpZT