In an age where our digital lives intertwine seamlessly with everyday activities, the threat of phishing attacks lurks in the shadows, waiting for the unsuspecting. As these deceptive tactics grow more sophisticated, knowing how to outsmart them becomes not just a skill, but a necessity. With every click and keystroke, we open the door to our personal information, making it essential to equip ourselves with knowledge and strategies to safeguard our online presence. Let’s embark on a journey to uncover the tools and techniques that empower us to recognize, resist, and ultimately conquer the phishing threats that seek to undermine our digital integrity.
Table of contents
ToggleUnderstanding Phishing Attacks
Phishing attacks are deceptive tactics used by cybercriminals to trick individuals into revealing sensitive information, such as passwords, credit card numbers, and personal identification details. These attacks often come in the form of emails, text messages, or websites that mimic legitimate entities, making it easy for unsuspecting users to fall victim.
Understanding the different types of phishing attacks is crucial for protection. Here are a few common types:
- Email phishing: The most recognized form, where attackers send emails that appear to come from trustworthy sources.
- Spear phishing: A targeted attempt aimed at specific individuals or organizations, leveraging personal information to increase credibility.
- Whaling: A high-stakes form of spear phishing targeting senior executives and high-profile individuals.
- Smishing: Phishing attempts through SMS; attackers send texts that prompt users to click links or provide information.
- Vishing: Voice phishing, where attackers use phone calls to extract confidential data by posing as legitimate entities.
Phishing attacks exploit human psychology, using urgency or fear to manipulate individuals into acting quickly without caution. Typically, these messages may threaten account suspension, unauthorized transactions, or enticing offers that seem too good to pass up.
To protect your digital life from phishing attacks, consider the following strategies:
- Scrutinize the sender’s email address: Check for minor misspellings or unusual domain names.
- Avoid clicking on links: Instead, visit websites directly by typing their URL in the browser.
- Enable two-factor authentication: Adding an extra layer of security can prevent unauthorized access.
- Keep software updated: Ensure that your operating system, applications, and antivirus software are up to date.
- Educate yourself: Familiarize yourself with common phishing tactics and how to recognize them.
Staying vigilant and informed about potential threats plays a vital role in defending against phishing attacks. By recognizing the signs and implementing protective measures, you can significantly reduce the risks associated with these online threats.
Types of Phishing Scams
Phishing attacks are a deceptive menace lurking in the shadows of the internet, aiming to snare unsuspecting victims. By masquerading as trusted entities, these scams manipulate emotions and exploit human psychology. Understanding the nuances of phishing is crucial to defend against it.
Types of Phishing Scams can vary widely, each with its unique approach to trick individuals. Here are some of the most common varieties:
- Traditional Phishing: This involves mass emails that appear to come from reputable organizations, requesting personal information.
- Spear Phishing: Unlike traditional phishing, this targeted approach focuses on a specific individual or organization, often using personal details to appear credible.
- Whaling: A sophisticated form of spear phishing, whaling targets high-profile individuals, such as executives or decision-makers, often with greater stakes involved.
- Vishing: This voice phishing uses phone calls to deceive victims into providing sensitive information, impersonating legitimate entities.
- Smishing: SMS phishing, or smishing, sends fraudulent text messages that can direct victims to malicious sites or entice them to respond with sensitive data.
To effectively fortify your defenses against these diverse threats, staying vigilant and informed is paramount. Recognizing the warning signs and learning how to verify communications can drastically reduce your risk of falling prey to phishing attacks.
Common Tactics Used by Attackers
Phishing attacks have become a pervasive threat in our digital world. Understanding the intricacies of these attacks is the first step to securing your online presence. At its core, phishing involves manipulating unsuspecting users into divulging sensitive information by posing as a trustworthy entity.
Common tactics employed by attackers can take various forms, each designed to exploit human psychology and technology vulnerabilities. Here are some frequent strategies:
- Email Spoofing: Attackers often send emails that appear to be from reputable sources, such as banks or popular services, misleading recipients into clicking links or downloading malicious attachments.
- Urgent Messages: Many phishing attempts create a false sense of urgency, warning victims that immediate action is required to avoid dire consequences—like account suspension or security breaches.
- Imitation of Branding: Cyber criminals meticulously mimic the design elements of legitimate websites and communication styles, making it challenging to differentiate between real and fake.
- Social Engineering: Phishing can leverage information gleaned from social media or previous interactions to craft personalized messages, increasing the likelihood that the victim will respond.
By familiarizing yourself with these tactics, you can start to identify suspicious activity and protect your digital life from potential threats. Stay vigilant and always question unexpected requests for information.
Best Practices for Prevention
Phishing attacks are deceptive techniques used by cybercriminals to steal sensitive information. To outsmart these schemes, it’s essential to adopt proactive measures that enhance your digital safety. Here are some best practices for preventing phishing attempts.
First and foremost, remain vigilant. Always double-check the sender’s email address. Phishers often use addresses that mimic legitimate sources but may contain slight alterations, such as extra letters or different domains.
Enable two-factor authentication wherever possible. This additional layer of security significantly reduces the chances of unauthorized access even if your password is compromised.
When in doubt, do not click on links or download attachments from unknown sources. Phishing emails frequently contain malicious links that lead directly to fraudulent websites. Instead, type the URL directly into your browser to ensure you are visiting a legitimate site.
Educate yourself about the different types of phishing attacks, including:
- Email Phishing: The most common form, involving fake emails that appear to be from legitimate organizations.
- Spear Phishing: Targeted attacks aimed at specific individuals or organizations, often using personal information to gain trust.
- Whaling: A sophisticated form of spear phishing that targets high-profile executives or significant individuals.
Regularly update and install security software on your devices. Keeping your systems up to date with the latest security patches can fend off many potential threats before they even reach you.
Always look for signs of a secure website, such as “https://” in the URL and a padlock icon. These indicators can help you identify legitimate sites.
Lastly, stay informed. Cyber threats are continuously evolving. Follow trusted resources to learn about the latest phishing techniques and how to counteract them effectively.
Recognizing Suspicious Emails
It’s essential to stay one step ahead of cybercriminals by recognizing suspicious emails. These deceptive messages can easily slip through the cracks if you’re not vigilant. Here are some key indicators to help you identify potentially harmful emails:
- Unusual sender addresses: Always check the sender’s email address. Look out for slight misspellings or domain variations that seem off.
- Generic greetings: Emails that begin with “Dear Customer” instead of your name can be a red flag.
- Urgent requests: Be cautious of emails that create a sense of urgency, asking for immediate action or personal information.
- Suspicious links: Hover your mouse over links to preview the destination. If it doesn’t match the email source, don’t click!
- Attachments from unknown sources: Avoid opening attachments from unfamiliar senders, as they may contain malware.
By familiarizing yourself with these signs, you can better shield your digital life from phishing attacks.
Practicing best prevention strategies will further fortify your defenses against these online threats. Consider implementing the following:
- Enable multi-factor authentication: This adds an additional layer of security, making it more challenging for attackers to gain access to your accounts.
- Regularly update passwords: Use strong, unique passwords for different accounts and change them periodically.
- Educate yourself: Stay informed about the latest phishing techniques and scams by following reputable cybersecurity sources.
- Utilize security software: Invest in reliable antivirus and anti-phishing solutions to detect and block threats.
Implementing these practices can significantly reduce your risk of falling victim to phishing scams, empowering you to navigate the digital realm with confidence.
Using Technology to Your Advantage
Phishing attacks are becoming more sophisticated, targeting individuals and organizations alike. To outsmart these threats, it’s crucial to develop a strong sense of vigilance and employ several strategies for defense.
One of the best practices for prevention is to stay informed about the latest phishing trends. Regularly updating your knowledge helps you recognize suspicious emails or messages. Look for common red flags, such as:
- Generic greetings like « Dear Customer. »
- Urgent requests for personal information.
- Unusual URLs or email addresses.
- Spelling and grammatical errors.
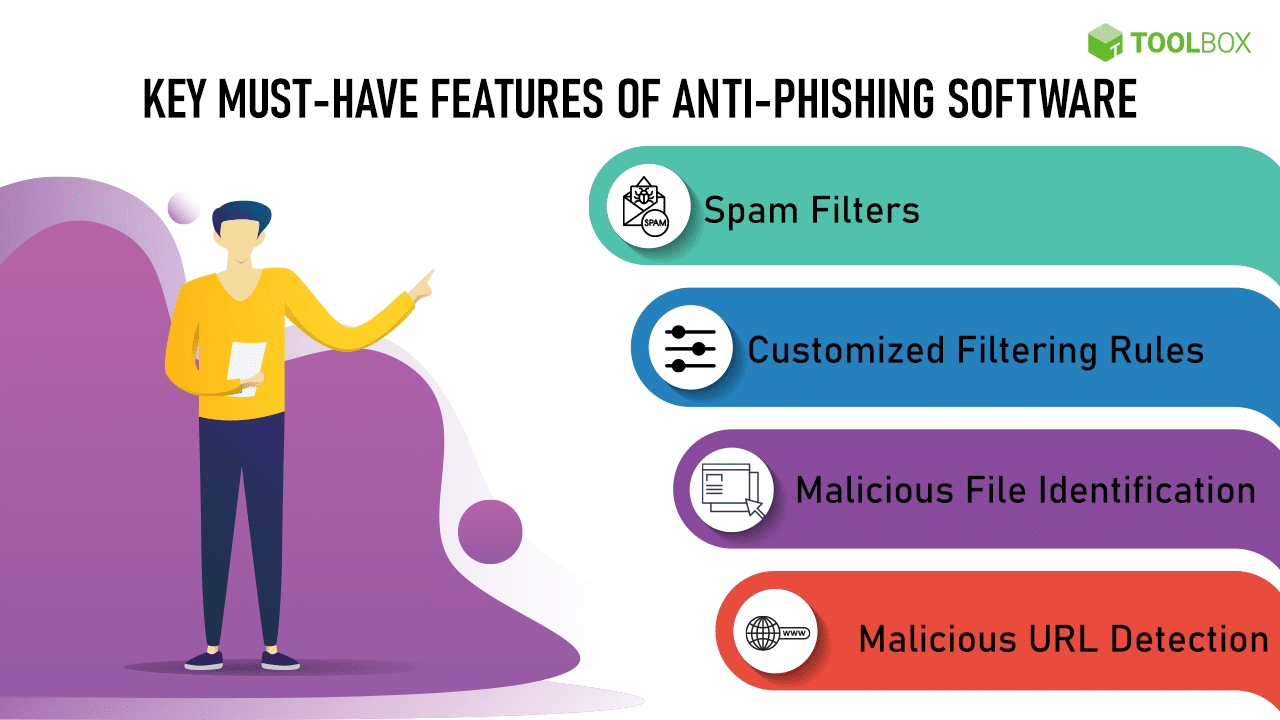
Another effective measure is to use technology to your advantage. Implementing security tools can significantly enhance your protection against phishing attempts. Here are some tools you should consider:
- Email filters: Utilize advanced spam filters that can automatically detect and divert potential phishing emails to a separate folder.
- Antivirus software: Ensure you have robust antivirus programs that can identify and block phishing websites.
- Password managers: Employing a password manager allows you to generate and store strong passwords securely, minimizing the risk of exposure.
- Multi-factor authentication: Always activate this feature where available to add another layer of security to your accounts.
Frequent updates to your devices and applications also help protect against vulnerabilities that phishing attacks can exploit. Enable automatic updates to ensure you always have the latest security patches.
Lastly, develop a habit of routinely reviewing your online accounts for any unauthorized transactions or changes. The sooner you catch any irregularities, the better your chances of mitigating potential damage.
Responding to a Phishing Attempt
Phishing attacks are more sophisticated than ever, targeting even the most cautious internet users. When you suspect a phishing attempt, it’s crucial to respond swiftly and wisely. Here are some steps to follow:
1. Assess the Situation: Take a moment to evaluate the message or communication you received. Look for red flags such as:
- Generic greetings instead of your name.
- Unusual or suspicious links.
- Urgent language that prompts immediate action.
2. Don’t Click! Resisting the impulse to click on suspicious links is essential. Instead, hover over the link to see the actual URL. If it looks strange, it probably is.
3. Verify the Source: If the message claims to be from a reputable organization, go directly to their official website or contact their customer service. Do not use the contact information provided in the suspicious message.
4. Report the Attempt: Most organizations take phishing attempts seriously. Report any suspicious messages to:
- The organization being impersonated.
- Your email provider.
- Local cybersecurity authorities or platforms like the Anti-Phishing Working Group.
5. Update Security Measures: Ensure your security software is up to date. Consider enabling features such as:
- Two-factor authentication.
- Spam filters.
- Regular password changes.
6. Educate Yourself: The more you know about the latest phishing techniques, the better prepared you’ll be. Frequent updates on phishing trends can strengthen your defenses.
Acting promptly and thoughtfully when faced with a phishing attempt can safeguard your personal information and digital life. Stay vigilant and informed!
Steps to Take Immediately
Phishing attempts can feel like an unexpected slap in the face, leaving you vulnerable and questioning your digital choices. When you encounter a phishing email or message, your immediate reaction can significantly influence the outcome. Here are some essential steps to take immediately if you suspect you’ve been targeted.
Don’t Panic. The first step is to remain calm. Phishing attempts are designed to create urgency and fear. By taking a deep breath, you can think more clearly and act wisely.
Do Not Click Any Links. Avoid interacting with any links or downloading attachments. These could lead you to malicious sites or compromise your device with malware.
Verify the Source. Look closely at the sender’s email address or phone number. Often, phishing attempts come from addresses that look similar to legitimate ones, but contain slight variations. If in doubt, reach out to the organization directly using contact information from their official website.
Report the Attempt. If you identify a phishing attempt, report it immediately. Notify your email provider, IT department (if applicable), or the organization being impersonated. Reporting helps protect others from falling victim.
Change Your Passwords. If you inadvertently clicked a link or provided personal information, change the relevant passwords right away. Use strong, unique passwords and consider enabling two-factor authentication for added security.
Run a Security Scan. Use antivirus or anti-malware software to perform a thorough scan of your devices. This can help identify and eliminate any potential threats that may have slipped through.
Educate Yourself. Familiarize yourself with common phishing tactics. The more you know, the better equipped you’ll be to recognize and avoid future attempts.
Staying aware and informed while navigating your digital life is crucial. By proactively responding to phishing attempts, you can safeguard your personal information and maintain a secure online presence.
Reporting and Recovery Options
When you encounter a phishing attempt, swift action can greatly mitigate damage. The first step is to remain calm and avoid interacting with any suspicious links or attachments. Often, the primary goal of these attacks is to steal your personal information or compromise your accounts.
Once you recognize a phishing attempt, it’s crucial to report it immediately. Most organizations provide a dedicated email or online form for reporting phishing. By reporting, you help them to take action against the perpetrator and protect others from falling victim.
Here are several methods for reporting phishing:
- Email Provider: Report the email to your email service provider.
- Company or Service: If the phishing attempt impersonates a specific company, inform them through their official website.
- Government Agencies: In many countries, you can report phishing attacks to a government agency that handles fraud.
- Anti-Phishing Organizations: Organizations like the Anti-Phishing Working Group can be helpful in tracking and combatting these scams.
After reporting the phishing attempt, consider your recovery options. If you clicked on a link or provided any personal information, take these steps:
- Change Your Passwords: Update passwords for your accounts, especially those that may have been compromised.
- Enable Two-Factor Authentication: This adds an extra layer of security that makes it harder for attackers to access your accounts.
- Monitor Your Accounts: Keep a close eye on your bank and online accounts for any unauthorized activity.
- Consider Identity Theft Protection: Services that monitor your personal information can help protect your digital life.
Proactively managing your online security and responding promptly to phishing attempts can greatly enhance your digital safety.